Evaluating cloud vendors using Zero-Trust security principles (Part 3)

Simon Morse
Technical Director Security, Versent

Simon Morse
Technical Director Security, Versent
In my previous article What is Zero Trust & why is it so important? (Part 1) we saw how cybersecurity thinking has evolved over the last few decades to arrive at today’s nuanced approach.
In article 2 of this series – How do we define Zero Trust? Hint: it’s not a one-size-fits-all solution (Part 2) – we looked at how Zero Trust cybersecurity principles are used to defend against emerging threats and busted some common Zero Trust myths.
In this article – part 3 – we’ll start putting all of that theory into practice by looking at a common challenge organisations face: how to manage risk in public cloud adoption. We’re not going to dive into the design and configuration of cloud components in this article. Instead, we’re going to talk about evaluating the security posture of cloud vendors themselves.
Zero Trust & cloud adoption
Changing platforms from a server-based on-premises setup to a decentralised cloud environment is a challenging process from a security point of view. The end result should provide a more resilient platform, but the transition involves making careful decisions to ensure compliance and security.
By the way: I’ll be referring to Amazon Web Services (AWS) in various sections of this article because that’s the platform I’ve personally worked on the most. But, Zero Trust principles can be applied broadly to all cloud providers.
The architecture of cloud platform security
To start this discussion, let’s look at the AWS cloud security responsibility model. Every cloud provider advocates a similar model, and they all have a common goal: to make the user/provider trust relationship explicit.
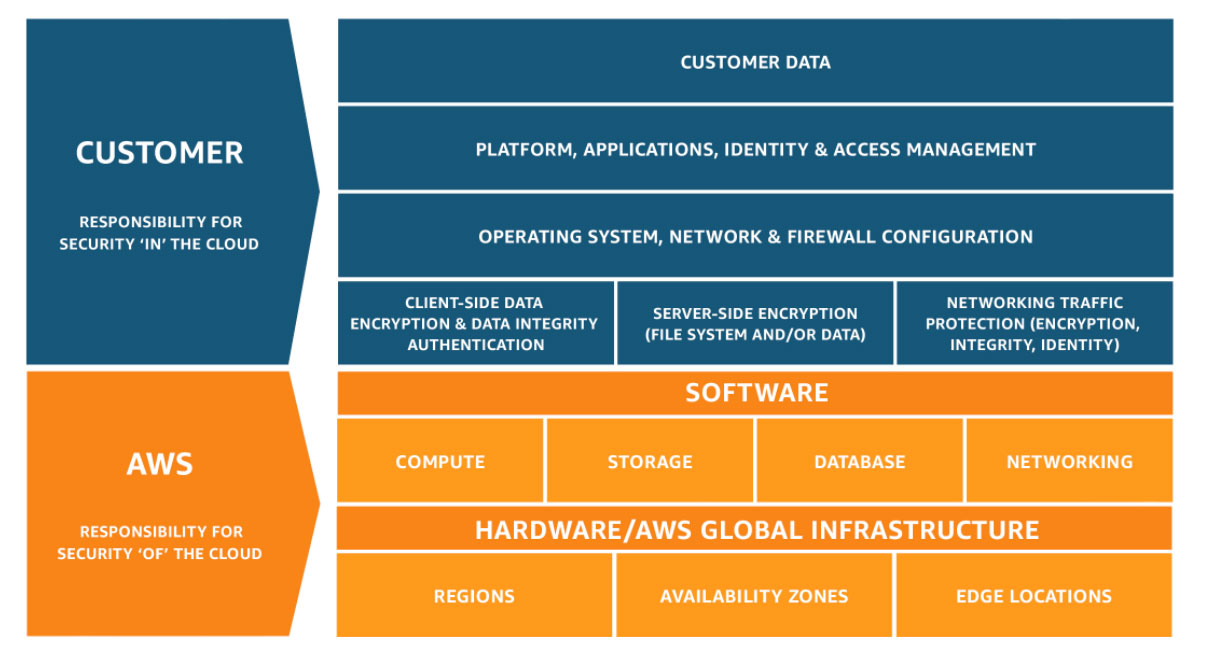
Looking at the AWS responsibility model above, it’s valid to ask; what makes a particular cloud provider trustworthy?
Which vendors can we trust?
When you’re assessing a cloud provider’s security posture, you don’t necessarily start with a detailed examination of the technology. It’s a good idea to step back and look at the provider’s broader security profile.
As in any supply chain management situation, you should make an independent evaluation of the extent to which you’re prepared to trust a particular provider and for what use cases. To make your assessment, you can look at the vendor’s published details, industry certifications, and independent testimony from external auditors. If we’re doing Zero Trust properly, we need to support our opinions with facts: third-party testimonials, industry peer review, or direct discussions with vendors.
Asking the right security questions
When I help organisations evaluate their cloud security situation and strategic options, I start by focusing the conversation on a few vital topics that I’ll outline below.
Vendor service management standards
Technical competence metrics that speak to cloud providers’ ability to run their IaaS, PaaS or SaaS solutions are a vital consideration when assessing a cloud vendor. This is the bread and butter of the public cloud value proposition. By virtue of scale, the big players like AWS and Azure typically do a much better job of this than smaller independent companies and usually at a more attractive price point, too.
HR controls: can we trust the people?
This is all about ensuring that the vendor we’re looking at uses appropriate measures such as background checks to ensure that their staff are trustworthy. We also need to make sure that the vendor’s team members are appropriately remunerated so that they don’t become “disgruntled employees”; a common vector for internal data breaches that can bypass even the most sophisticated security measures.
Legal jurisdiction
Legal requirements and restrictions are a serious consideration when we’re assessing a vendor’s suitability. The security credibility of a given cloud solution will vary a lot depending on the client’s industry sector, location, and the deployment footprint available.
Vendor viability in the longer term
When comparing cloud security providers, we need to be cognizant of how many have ceased to exist, shelved their offerings, or have been bought out over the last couple of decades. You don’t want to sign up to a vendor only to have them go out of business the following year. This issue also often comes up when organisations select a cloud provider and then augment that arrangement with specialist security or other operational tooling.
Next steps
Once you’re satisfied that a particular cloud vendor is trustworthy and meets the security requirements of your organisation, you can start thinking about your platform’s design and security configuration.
In my next article, I’ll talk about applying Zero Trust principles to strategic cloud security, getting into some detail on network vs account security paradigms and optimising tenancy models.

Get the right security advice
Whatever your role in organisational leadership, whether it be technology or human resources, we’re all responsible for making good security choices.
Sustainable risk management derives from a combination of cultural, ethical and technological imperatives. So, looking at cloud vendors through the lens of Zero Trust means assessing a broad range of characteristics.
Making well-informed security choices is no easy task, but partnering with a specialist advisor is a good first step.
Get in touch with a Versent advisor and take the guesswork out of your cloud security.