Versent’s Day2 DevOps Automation Monkey

Gopi Thiruvengadam

Gopi Thiruvengadam
The Problem Statement
In your journey to Cloud adoption one of the key aspects that is often overlooked is the consumption of the toolset that is available across the entire DevOps toolkit. Cloud vendors like Azure and AWS have published landing zone models that can be easily deployed to enforce guardrails around policies, connectivity and for establishing a repeatable and proven pattern for consumption of cloud resources within their environment.
However, when a team really wants to consume these resources – one or more request tickets are created and in a very large organization, this process will be multi-phased and there are gaps and inconsistencies with respect to how this is handled.
An Illustrated Scenario
The below is an example that outlines one such gap in a typical Enterprise where DevOps and Identity teams work in silos due to separation of duties.
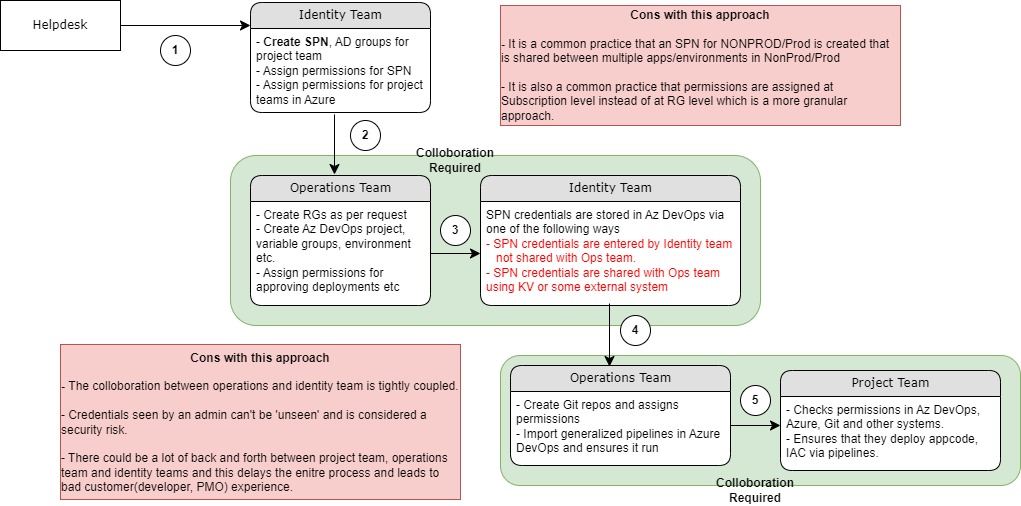
Identity Team Tasks:
- Creating an SPN (Service Principal Name) and required Active Directory (AD) groups for a Non-Production subscription.
- Assigning permissions for the SPN on Subscription or Resource Group (RG) level.
- Creating the required AD groups as required for permissions management.
DevOps Team Tasks:
- Creating necessary GitHub repositories and configuring permissions for AD groups or reusing existing groups.
- Collaborating with the Identity team to set up SPN credentials within the DevOps project, either through Service Connection or variable groups.
- Assigning appropriate permissions to Subscriptions, RGs and DevOps project along with importing foundation pipelines.
Challenges and Pain points:
- Collaboration: The need for DevOps and Identity teams to collaborate on setting up credentials and permissions can introduce delays due to coordination, communication and potential errors.
- Customised Tooling: While these steps can be automated using in-house scripts or solutions, such tools can become complex and specialised over time. A failure or bottleneck in this toolchain can hinder the entire process.
- Tooling Lifecycle Management: As the in-house tools become more sophisticated, they may require ongoing maintenance, updates and troubleshooting, which could potentially consume additional resources.
- Risk of Errors: Complex and manual steps increase the risk of human errors, potentially leading to security vulnerabilities or misconfiguration.
Overall, the proposed tooling should address the challenges outlined in the scenario above by providing a streamlined, automated and standardized solution for collaboration between DevOps and Identity teams, resulting in increased efficiency and reduced bottlenecks.
Proposed Solution
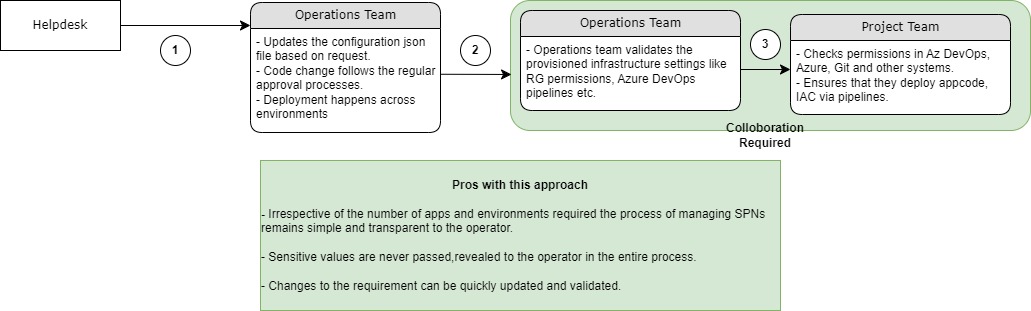
The proposed solution is to drive the entire process via code. More specifically to put Terraform at the heart of the infrastructure and with an optional HCP Vault component we can improve the overall security posture of this solution.
The entire requirements of application team onboarding to consume the cloud infrastructure can be codified so that the request ticket can be translated into readable JSON code and be deployed via automated process.
The below is a demonstration of what the current state looks like
The below is a depiction of what the future state could look like
Key Benefits
The proposed solution involves building a tool that offers several advantages:
- Rapid Enablement: The tool can be deployed quickly and can be further customized based on specific customer requirements. This speed of deployment ensures quick implementation and adaptation.
- Enhanced Security: The tool deploys Service Principal Names (SPNs) at runtime, and it separates the roles of Vault Admin, DevOps Admin, and Identity Admin. This segregation of duties makes it extremely difficult for any single admin to misuse admin credentials, enhancing overall security.
- Scalability and Flexibility: The tool’s codebase is designed to evolve over time. Additional features, such as integrating with Jenkins, Gitlab, and more, can be added to the toolchain. This extensibility makes it adaptable to the changing needs of the organization.
- Expanding Client Base: The tool’s versatility, demonstrated by its ability to integrate with various toolsets, means it can be marketed to a wider range of clients. This expansion of the target client base increases its potential impact and value.
- Simplified and Reliable Processes: The tool provides a unified approach to replace complex and error-prone methods currently employed by many clients. By offering a streamlined and standardized solution, it reduces the likelihood of errors and simplifies the overall process.
- Vendor Agnostic: By leveraging HashiCorp tools like Vault and Terraform Cloud, the tool remains agnostic to the underlying technology supported by Terraform. This ensures compatibility with various technologies and platforms, providing greater flexibility.
In summary, the proposed tool offers rapid deployment, enhanced security through role separation, scalability for future enhancements, broader market appeal, simplified processes, and technology agnosticism through the use of HashiCorp tools. These advantages collectively contribute to a more efficient and secure solution for the specified problem.
Show Me The Code
The details of this proposal can be found in the below link.
https://github.com/Versent/day2-automation-monkey Connect your Github account