The Road towards a Secure User Experience

Jenny Yang
Security Architect, Versent

Jenny Yang
Security Architect, Versent
Working in security, at times I feel like I am living a double life – one as an “all-knowing” consultant, the other as a hypocritical human being who makes mistakes and can sometimes be lazy. There are internal conflicts between ‘what we should do’ versus ‘what we actually do’. This has been traditionally portrayed a trade-off between security and user experience.
This shift in expectations has been driven by demand from both end-users (customers and enterprise employees) and from industry (for example companies such as Google, Facebook, UX design consultants and security professionals).
Identity and Access Management
One of the greatest improvements in user experience has been in the login experience. A customer’s identity and the access to their data is the treasure trove most hackers and modern day con-artists and scammers look for. If I count how many individual logins I store in my password manager to date, it is 409. That is not including the obscure ones I had pre-Facebook. When signing up for a new food delivery app, the easiest solution is just to re-use an old password that you have used for the last 7 years. This is a matter of convenience but is not necessarily right. Yet neither do I want to force myself to remember the 8 alphanumeric (upper and lower case, of course) and 4 special character gibberish every time I have to set up a new account setup. The adoption of social media platforms towards the mass market in developed countries has driven a significant increase in the development of an online social or personal identity. Often these platforms, take Facebook or Google for instance, have become the entry point to other services.
Whilst usernames and passwords may seem less exciting than other technologies, the mechanism by which you identify yourself and gain access to your accounts and information is evolving. With emerging technologies such as biometric authentication, user behavioral analytics, identity as a service, these tools are breaking down the barrier towards a more technically secure and frictionless user experience.
Inform your Users to Improve Trust
Whilst you can integrate the latest hashing algorithms into your product, it is ‘all-for-naught, when you have that one user who chooses to write their password on a post-it note next to their computer.
Leverage A/B testing as a mechanism to scour for data into how users will behave and whether they will adhere your security tips and warnings. Encourage users to do the right thing by making the default, the secure option. In a recent example with Google, the user experience and security team tested opinionated designs (UI designs with a preferred option as seen below).
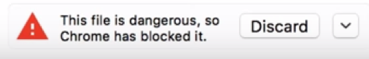
Clear indications with limited alternative options will encourage users to go down the right path. In doing so, users have an improved level of trust with the company. Though use this sparingly, as false positives will undermine credibility and users will be subject to warning fatigue i.e. ignore your security warnings.
Equip your Developers
Often, the most effective security controls are transparent to the user. The magic you see on screen and what occurs behind the scenes is controlled by the developers. One of the core goals good software developers aim to strive for is a stable foundation. Whilst functionality is often at the forefront of the developer’s mind, as it should be, even the most technically skilled and literate developers can make mistakes. If we are looking at starting with a strong foundation, then activities such as black box testing and automated scanning tools to check for code coverage and code quality will equip developers to produce better code over time. It also gives a standard baseline the development teams can work towards whilst maintaining a secure code posture. Automation is a key enabler for making developers lives easier, better and is much more scalable. If we take Atlassian as an example, a software development company where millions of lines of code are deployed each week and only a handful of security engineers. Automation, secure code quality and security controls
Final Notes
User experience and security can no longer be portrayed as a trade-off or a binary option. The balancing act between user experience and security will be tough and yes, even on the best of days, we are human and we will make mistakes. If the intention is to design for the user, then there must be the intention to protect the user. With new tools to leverage and new techniques to try out, we can slowly look at closing the gap between user experience and security. After all, in this day and age, we no longer need to sacrifice user experience for security. In the long run, a business that focuses both upon user experience and security will build a product that customers can trust and believe in. Operating in a competitive climate, customer loyalty and retention will drive these businesses to be more likely to flourish and be sustainable in the future.
