The Path to Production is Paved with Good Intentions

Simon Douglas
Program Director

Simon Douglas
Program Director
When you click on your news feed, or receive a message from a company that has just been hacked; apart from asking “how did this happen”, the next question is how can I protect my organisation, customers and people from experiencing such a breach now and into the future?
In Australia alone, an estimated 55% of Australians aged 15 years and over (11.1 million) were exposed to a scam in 2020-21[1] and 11% of Australians experienced personal fraud in 2020-21, up from 8.5% in 2014-15[2].
The latest breach from a national telecommunications carrier has seen up to 9.8 million customers’ data compromised[3]. This is the latest in a growing prevalence of ongoing data theft and personal fraud which is a global problem; the attacks are relentless, and the need for data integrity and security is paramount.
With the evolution of data as a currency in line with our customer’s greater reliance on digital technology, there has been a greater emphasis on security, not just in Production systems but also in Development systems, to ensure critical Personally Identifiable Information (PII) data is secured and only available to the appropriate persons within organisations. That said, a report published by Cybersecurity Insiders states up 77% of employees have more access privileges than required for their jobs[4] which indicates a need to further improve access to PII data, not just externally but internally as well.
How exposed is my organisation?
Let’s take a look at just some of the available tools in the following image [5] utilised in the modern SDLC with the introduction of CICD with the mindset of security and protection of PII data. On their own, and even integrated these may be well secured to be sure; however, how they are integrated and utilised, and by who, within your SDLC (Software Development Lifecycle) and STDL (Software Test Lifecycle) is an important consideration.

Now let’s consider a common environments pattern and the way these environments are managed across your SDLC.
- Dev – Either conducted in a secure cloud environment or most commonly conducted on local machines.
- Test – A set of environments to execute Integration testing to validate functionality.
- Staging – An environment cluster to support non-function testing, Stress and Volume, Performance and Penetration testing.
- Production – Your public environment and the most stringently secured.
Can you categorically state you have complete confidence that your data is secure across your technology ecosystem? You should unequivocally be able to answer “yes”.
There have been numerous and often very public examples of the failure to protect PII data, both in Production as well as within non-production environments. The cost of doing nothing in ensuing best practices in securing data across your entire ecosystem is high in both financial and reputational damage that can be difficult, if not impossible to recover from.
The need to be faster, and release features and functionality continuously causes a tug-of-war in the battle between speed to market, efficiency in development and security exposure to malicious intent, employee error. This is further compounded by the complexity of decentralisation of accountability, use of numerous open-source tools, use of complex architectures that span varying data-center and cloud topologies and configurations and the globalisation of Development and Operations.
Often the biggest risk is the one your organisation may be the least aware of and therefore most vulnerable to; within the SDLC where poor practices, shortcuts, and human error can leave you exposed. The thread of attack is relentless, so your organisations view of security needs match that of the threat. This means your security and monitoring need to be continuous, dynamic and relentless.
What does my organisation need to do?
A recent article published points to the fact that “Current network security concepts in the cloud don’t work well”[6] and this is due to the fact many Zero Trust policies are focused on static runtime protection with no consideration of the development lifecycle or any aspect of event management capability.
When considering DevSecOps across the Software Development Lifecycle (SDLC) we need to consider the entirety of actors; human and machine and how we are securing the ecosystem and the data within. For this to occur we need to move beyond static monitoring toward dynamic monitoring of the SDLC to ensure “situational awareness of the Zero Trust implementation collected from the User, Device, Network/Environment, Application & Workload, and Data components. This information is used to identify potential threats which will result in dynamic changes to the security policy and access decisions” [7]
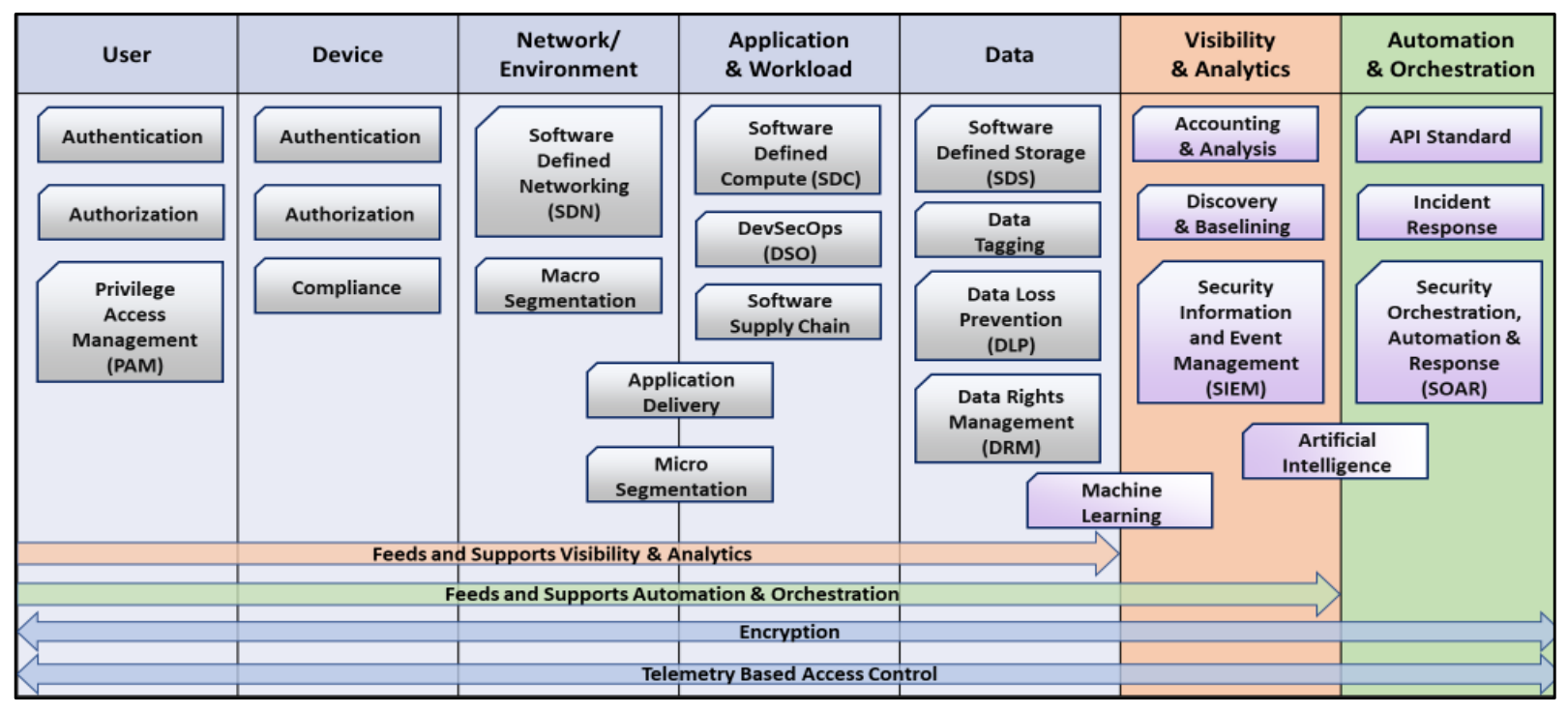
Access to PII data should be strictly controlled, tightly governed, and above all else impenetrable to malicious interception. As an example, in development Production data being made available in lower environments for development and testing without hygiene activity such as data obfuscation being applied is a risk. This simple process of data obfuscation protects any data being inadvertently, or by deceitful intent, being made available and putting your organisations customer’s PII data at risk.
As organisations have shifted to Continuous Delivery; and for some Continuous Deployment; to ensure speed and efficiency is balanced with quality, it is critical to execute comprehensive testing through the Continuous Integration (CI) cycle prior to release. This requires pre-production environments to reflect production to ensure comprehensive testing can be executed in a “production-like” environment. Stress and Volume (Performance) as well as Integration, Penetration, and Verification testing to validate both function, performance and security as close to the Production environment as possible is critical. Simulations and emulations can take you so far, confidence is gained knowing you have tested like for like. Further to this, most organisations are now operating multi-state production environments, A/B or Blue/Green and deploying Features either dormant, that are “toggled off”, or executing canary releases, or deploying Features continuously (and often a combination of all of these). This complexity in release and environment management requires your organisations security posture to be dynamic and embedded across your organisations SDLC. Further to this the need to minimise environments to reduce cycle times and Feedback loops to escape from large-scale test-cycles means that this comprehensive testing needs to occur as close to the development lifecycle as possible through comprehensive test-automation and execution that collapses these test windows from weeks to hours. But like-for-like doesn’t mean exact! Copying Production data is not an advisable practice as it can breach your organisations policies or worse; breach Industry or Government regulation, exposing your organisation to potential penalties or litigation. Fast and efficient doesn’t mean take shortcuts!
Furthermore, with the advent of open source technology, there needs to be governance applied to the SDLC ecosystem to ensure that the software being utilised adheres to all regulatory and security requirements and is adequately maintained to avoid the ongoing threat of pernicious activity conducted relentlessly to steal information and weaponise data for illegal gain.
How can Versent help?
At Versent we have a strong partnership with Ping Identity and other key zero trust partners, HashiCorp, Aqua Security, Cloudflare, and Dynatrace to ensure that we apply a Zero Trust methodology to your technology ecosystem. Further to this Versent has developed a Delivery framework to ensure that security, audibility, and governance are built into the SDLC (Software Development Lifecycle) and STDL (Software Test Lifecycle).
Aqua Security is leading the way in DevSecOps by shifting-left security into the SDLC to enable organisations to automate secure development and deployment of applications in their DevOps pipelines, by embedding comprehensive security testing and powerful policy-driven controls. With the shift to serverless architectures and use of containerisation there is a need to revisit the Security approach to protect your organisation from risks such as unsecured serverless deployment configuration, unsecured storage, overprivileged function permissions and roles, inadequate function monitoring, denial of service (DOS), and financial resource exhaustion by hijacking your own workloads for nefarious purposes (e.g., mining for crypto-currency). [8]
Hashicorp is a leader in Zero-trust in modern cloud infrastructure with its focus on shifting from static and IP-based; defined by a perimeter security (great for DC; not for Cloud), to dynamic and identity-based; with no clear perimeter (ubiquitous) to ensure access is based on trusted identities. HashiCorp’s approach to Zero-trust incorporates HashiCorp Vault for Machine Authentication & Authorisation, HashiCorp Consul to enable machine-to-machine access by enforcing authentication between applications and ensuring only the right machines are talking to each other, and HashiCorp Boundary that provides simple, secure remote access to securely access dynamic hosts and services without managing credentials, IPs, or exposing your network. [9]
Ping Identity is our partner in Identity and Access Management. Ping Identity secures all your organisations primary access management use cases, including customer, workforce, partner and Internet of Things (IoT). The Ping Intelligent Identity Platform provides secure single sign on (SSO), adaptive multi-factor authentication (MFA), security control for applications and APIs and, personalised and unified profile directories (Directory).
Cloudflare is leading the charge in securing your network from unknown risks to data and customer accounts. Application architectures have become increasingly distributed and decentralised for performance and resilience, alongside the complexities of a mixture of on-premise and cloud-based services, as well as securing an increasingly mobile and remote workforce. Cloudflare offers Secure Access Service Edge (SASE), combining network connectivity services with Zero Trust security services on one of the fastest, purpose-built global networks available. Cloudflare provides Zero Trust Network Access, Secure Web Gateway, WAN as a Service, Cloud Access Security Broker, Firewall as a Service and Cloudflare Network. [10]
Dynatrace continues to lead the way in Observability and Monitoring with coverage of the entire ecosystem to deliver a Simple Pane of Glass across a complex ecosystem that spans, Infrastructure monitoring, Application and Microservices, Application Security, Digital experience, Business Analytics, and cloud automation to provide automatic and intelligent observability supporting todays multi-cloud technology mix. [11]
At Versent we do DevSecOps because we understand the cost of doing nothing can cause significant financial, reputational and brand damage; often without realising it. We know this gap can exist as a dormant exposure in your Software Development Lifecycle (SDLC) and we know how to provide protection from DevOops…
At Versent we enable you to execute with Speed, Efficiency, Securely and without compromise to Quality through our tailored DevSecOps approach with the four key tenants of:
- Single Source of Truth | Change Management linking CMDB at the component level, linked to Features to be developed
- Steel Thread of Decomposition | Trace your Feature from Vision to Value with full auditability
- Security with Zero-trust | trust no one, verify everything
- Simple Pane of Glass | Observe and Monitor what is necessary and important, continuously
With these guard-rails in place your organisation will achieve Speed and Efficiency with high confidence in your security posture and without compromise to Quality; ensuring your organisation and the data under your stewardship is safe.
If you want to know more about how Versent can help your organisation avoid DevOops, and embrace DevSecOps to secure your ecosystem both directly through Identity and Access Management as well as indirectly by applying best practice security design to your Infrastructure, Cloud, WebApps, and across the SDLC please reach out and we will help you determine your organisations risk, and help you plug the holes to protect your organisations most valuable asset; your customers.
Simon Douglas
Program Director, Versent
simon.douglas@versent.com.au
[1] Personal Fraud, 2020-21 financial year
[2] Personal Fraud, 2020-21 financial year
[4] 2021 Identity and Access Management Report [Core Security by HelpSystems) – Cybersecurity Insiders
[5] James Bowman
[6] How Zero Trust Security Revolutionizes DevSecOps
[7] https://apps.dtic.mil/sti/pdfs/AD1145432.pdf
[8] DevSecOps: Making it Happen
[9] https://www.datocms-assets.com/2885/1602637867-zerotrustwhitepaperv4digital.pdf