How to harness AWS best practices with the Well Architected Framework

Josh Lopez
Partner Cloud Adoption, Versent

Josh Lopez
Partner Cloud Adoption, Versent
Versent is now an AWS approved Well Architected Partner, and we have built a dedicated practice to offer our customers AWS Well-Architected Reviews, that is completely complimentary.
At Versent, the AWS Well-Architected Framework is used to help customers build the most secure, high-performing, resilient, and efficient infrastructure possible for every type of application.
The framework provides a consistent approach to evaluate AWS architectures and provide guidance to implement designs that will scale as the ecosystem of services in AWS scale. The framework is built around five pillars;
- Operational Excellence Pillar – focuses on the ability to run and manage applications to ensure they’re delivering constant business value.
- Security Pillar – a very important pillar to all our customers and its focus is on the ability to protect data and applications while continuing to delivery business outcomes.
- Reliability Pillar – focuses on how your application has been architected to recover from failure and mitigate these failures to recover itself.
- Performance Efficiency Pillar – is how your application meets the needs of your customers by efficiently scaling when demand changes.
- Cost Optimisation Pillar – how you effectively manage and eliminate any unneeded costs in running your application.
Assessing architecture against the Security Pillar using the AWS Well Architected Framework
In this blog, I’ll focus in on the Security Pillar and use a reference architecture to showcase some best practices when architecting in AWS.
The reference architecture I’ll use for this will be an internet facing three tier web application where I’ve highlighted in green boxes various aspects of the architecture that demonstrate best practices against the Security Pillar of the Well Architected Framework.
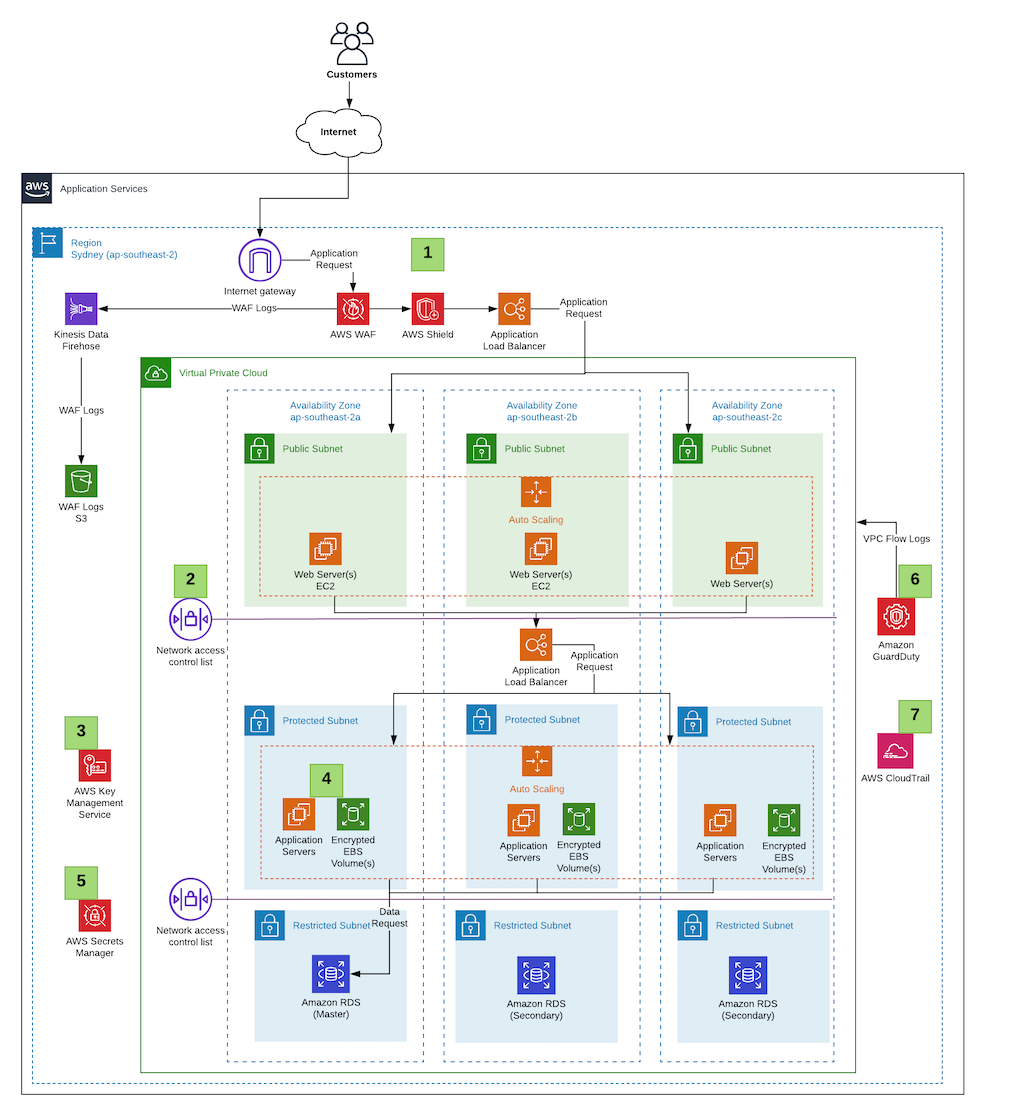
- For internet facing applications, it’s very important to ensure that you’re protecting the front door of your application. AWS WAF has been used to protect against malicious attacks and also AWS Shield to provide the layer of defence against Distributed Denial of Service (DDoS) attacks.
- To segregate network boundaries of control, AWS Network Access Control Lists (NACL) are used in between subnets to ensure only the traffic that is permitted will flow.
- AWS Key Management Service (KMS) will provide the ability to encrypt data at rest for services such as AWS Elastic Block Storage (EBS) and Amazon Relational Database Service (RDS).
- As Amazon CTO Werner Vogels says ‘Dance like nobody’s watching. Encrypt like everyone is’. It’s very important to encrypt everything and in this architecture, AWS KMS is used to encrypt everything from the AWS EBS Volumes attached to each AWS EC2 instance to the Amazon RDS instances.
- Passwords often find themselves in configuration and this can lead to data leaking into the hands of people who shouldn’t have it. To make the management of this seamless, AWS Secrets Manager has been used which has native support for AWS RDS to easily manage the rotation and delivery of credentials to the privileged resources that require them.
- Network traffic can be hard to keep a track of and filter through if all traffic that’s traversing your application is in fact authorised and non-malicious. To intelligently detect any threats in the network, AWS GuardDuty has been enabled to continuously inspect the VPC Flow Logs and alert if any malicious behaviour is detected.
- Last but not least to ensure that all API calls within an account are logged it’s important to enable AWS CloudTrail to provide governance over the actions that are performed.
This list is in no way an exhaustive list and the more security that’s in place the better. Security in AWS is job zero for everyone and customer data protection is paramount.
How we can help to assess your architecture against the Well Architected Framework?
As AWS Well Architected Partners, we can help by performing a Well Architected Review which is complementary to our customers.
A Well Architected Review is a 2-3-hour workshop where we use the AWS Well Architected Tool to assess your architecture against the framework. This involves one of our Well Architected Practitioners going through each pillar with you to determine if your architecture is in fact Well Architected. Performing regular Well Architected Reviews really help our customers build the most secure, high-performing, resilient, and efficient infrastructure possible for their applications.
If you’d like one of our Well Architected Practitioners to assist in reviewing your architecture, please contact us here: https://versent.com.au/#contact
If you’d like more info, check out this great blog from AWS on the Well Architected Framework.