Privileged Account Management in AWS

Richard Keit
Principal Solution Architect

Richard Keit
Principal Solution Architect
In the lead up to the annual AWS re:Invent conference, one of the most frequently asked for features has been released and we couldn’t be happier to see it released.
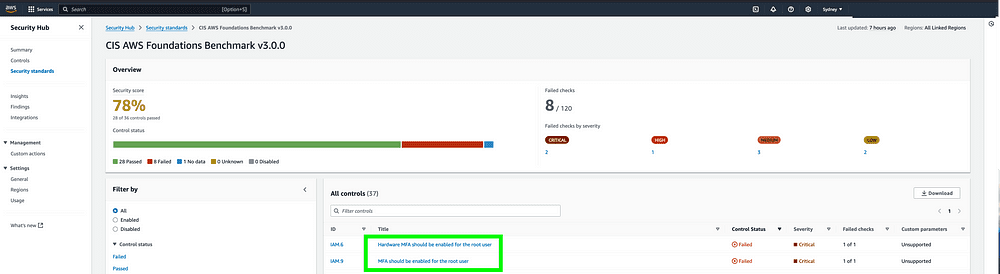
AWS has released centralised root account management for AWS accounts in an AWS Organization. This feature allows the ability for the privileged account, known as the root user, to be removed from the account while also restricting the ability to restore the credential.
While creating member accounts in an AWS Organization, the Management Account does not need to have access but up until now — the member account would be created for the root user with an unknown password. This would violate compliance checks from a multitude of frameworks prompting for multi-factor authentication to be enabled for the user. Resolution of these checks would require for a password reset flow, then ultimately the operations team would be responsible for managing the security of this account.
Configuration of Managing Root Access Management
When logging in the Management Account, users are presented with refreshed IAM console and a new feature “Root access Management”.

As with most AWS Organization features, it is considered best practice to delegated an Administrator account (other than the Management Account) for actions. In our example, we delegate this to the Audit Account — this is inline with AWS Control Tower and the delegation of security and governance tools to the Audit Account.


Initial configuration for existing member accounts
AWS Accounts created prior to this feature release already have Root users created, even if the password is unknown. Therefore for first configuration we will complete is to remove the root credential.
From the IAM console in the Management account, navigate to the “Root access management” option set (this was initially where configuration was completed).

Select any account that you wish to complete actions against, in our example we have selected the “LogArchive” account — this account is used by AWS Control Tower to centralized logging within the organization.



Initial release functionality
Day 1 release of the feature allows restoration of AWS S3 Bucket and SQS queue policies. In the event that users have configured a resource policy that restricts administration, the root user can be used to restore access.
Originally, this flow requires the reset of the root user which would then require management of the credential going forwards.
Central management now allows for these policies to be reset from the Management account directly, which is a fantastic improvement on the previous flow.

AWS has included a feedback form inline to prompt users for their feedback on features they’d like to see. We encourage you to provide your feedback on what you’d like to see released soon.
Even if the features you’d like to see aren’t there right now, temporarily, the operations team managing the AWS Organization can reset the password, complete the action and then remove the root user afterwards. This in itself provides more flexibility and security to existing operations.

We’re excited to see this feature released and are eagerly enabling this for our customers shortly.
Reach out if you’d like assistance with implementing this and other AWS best practices.