A Gentle Introduction to AWS Network Firewall: Part 1

Steve Jones
Principal Solutions Architect

Steve Jones
Principal Solutions Architect
Part one of a three-part series on AWS Network Firewall’s capabilities, architecture and operational considerations
Introduction
AWS Network Firewall (NFW) is a managed network firewall service designed to protect your Virtual Private Cloud hosted cloud resources and improve your overall network security posture. It’s an essential component in any Enterprise Multi-Account AWS Architecture, but as with all AWS services, it can be deployed in several ways.
This series will guide you through Network Firewall’s capabilities, architecture, and operational considerations. The first part will explore the architecture and core capabilities, their benefits, and their role within an AWS environment.
Overview
Network Firewall is a regional service that offers a range of security features to help organisations establish segmented network boundaries and protect against threats like malware, intrusions, and data exfiltration.
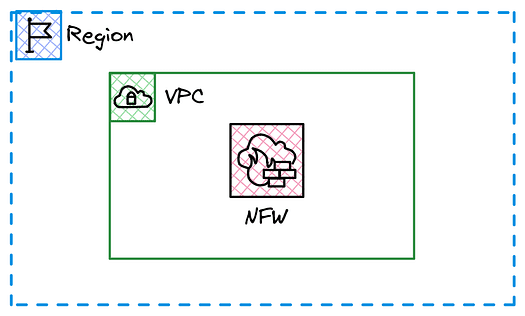
It supports managed and customisable rules, enabling the enforcement of tailored network security policies for both native and hybrid environments. The service can be deployed at various points in the network to protect on-premises, inter-VPC, and internet traffic (egress and ingress).
As a managed service, AWS Network Firewall reduces operational overhead by eliminating the need for teams to manage infrastructure, allowing them to focus on defining security policies. It also scales automatically with network traffic demands.
The service integrates with AWS Transit Gateway, AWS Firewall Manager, and AWS CloudWatch, enabling centralised deployment, consistent policy enforcement, and comprehensive traffic monitoring to support compliance and governance efforts.
Architecture Components
Firewall Endpoints
AWS Network Firewall endpoints are deployed into an Amazon Virtual Private Cloud (VPC). These firewall endpoints act as entry and exit points for network traffic, applying firewall rules to filter packets as they pass through.
These endpoints are built on top of AWS Gateway Load Balancer (GWLB), a service designed to deploy and scale network appliances, such as firewalls, across multiple Availability Zones (AZs).
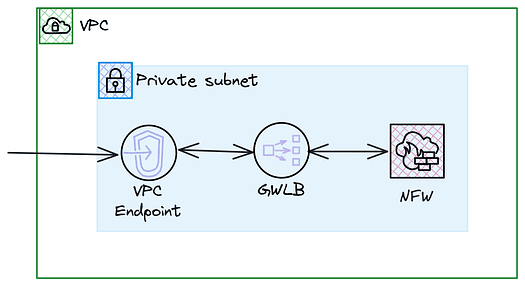
GWLB combines a transparent network gateway (that sits in line with your traffic) with a load balancer that distributes incoming traffic across healthy firewall instances managed by AWS.
This architecture offers several benefits:
- High Availability — By deploying firewall endpoints across multiple Availability Zones, AWS ensures that your firewall remains operational even if one AZ becomes unavailable.
- Automatic Scaling—Firewall endpoints automatically scale to match the traffic volume. This elasticity ensures your firewall can handle sudden traffic spikes without compromising performance or security.
- Transparent Deployment — GWLB and firewall endpoints are deployed transparently, meaning the firewall is integrated seamlessly into your VPC architecture without requiring changes to your applications or network configurations.
Route Tables
VPC route tables are configured to reference the firewall endpoints to direct traffic through the Firewall endpoints.
This setup involves:
- Route Table Configuration — Routes associated with your VPC subnets route specific traffic through the firewall endpoints. For example, route all outbound internet traffic or inter-subnet traffic through the firewall.
- Route Targets — These routes target the firewall endpoint’s ENI (Elastic Network Interface), presented as a VPC endpoint, ensuring that traffic is filtered according to the rules defined in the firewall policy.
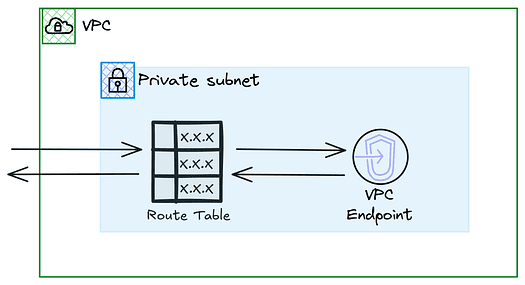
By configuring route tables to direct traffic through the firewall endpoints, you can use a transit gateway to enforce security policies consistently across your VPC or many VPCs.
Importance of Asymmetric Traffic
Asymmetric traffic occurs when the inbound and outbound traffic between two points in a network take different paths. This can pose challenges in the Network Firewall context because the firewall must process traffic flow within the same endpoint.
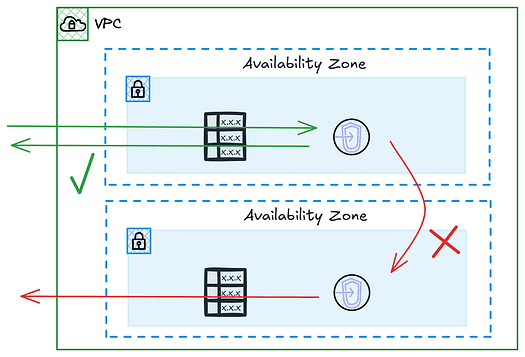
Symmetry in traffic flows is critical to ensuring the firewall operates effectively. This is achieved through consistent routing configuration, ensuring that both the inbound and outbound paths for a given session go through the same firewall endpoint.
Automation and using Infrastructure as Code avoid mistakes when establishing the correct routing within the Network Firewall VPC. Appliance mode set on the VPC attachment is necessary when connecting multiple VPCs via Transit Gateway.
Firewall Policy
A firewall policy dictates how traffic should be filtered and protected based on specific security rules defined in rule groups. These rule groups can consist of stateless and stateful rules, enabling fine-grained control over network traffic.
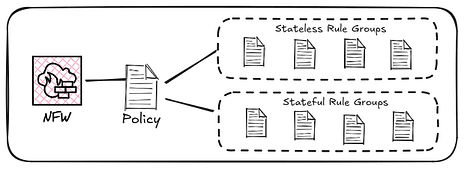
Stateless rules inspect individual packets in isolation, while stateful rules evaluate the entire context of a network session, such as the state of a connection and its traffic patterns.
An important aspect of configuring a Network Firewall policy is choosing between strict and default operational modes. These modes determine how the firewall handles traffic that does not explicitly match the policy’s rules.
Strict Mode — This mode only allows traffic that matches the rules explicitly defined in the policy. Traffic that does not match a rule is automatically dropped. Rules are ordered by priority within each rule group.
This model is highly secure because it ensures that only known, trusted traffic can pass through. However, comprehensive rule definitions are required to ensure that legitimate traffic is not inadvertently blocked. Strict mode is ideal for environments with highly sensitive data or critical applications.
Default Mode — Any traffic not matching an explicit rule in the firewall policy is allowed. This approach is helpful in scenarios where flexibility is needed and a desire to avoid disrupting legitimate traffic that might not yet be fully accounted for in the rule set exists.
AWS recommends using strict mode because it allows you to define the precise order in which the stateful engine evaluates your rules. It also makes traffic patterns known and explicit.
Rule Groups
Rule groups determine how the firewall inspects and processes network traffic. There are two types of rule groups: stateful and stateless.
Each type has specific use cases and can be further customised using managed and custom rule groups. Additionally, users can implement domain allowlists/blocklists and leverage Suricata rules for enhanced flexibility.
Each rule group has a user-defined capacity, which determines the number of rules it can contain. Consideration needs to be taken to size accordingly and for growth.
Stateless Rules
Stateless rules inspect individual packets in isolation without considering the context of a traffic flow. These rules are typically used for simple packet filtering based on basic IP protocol information, such as source and destination IP addresses, ports, and protocols.
Use Cases for Stateless Rules:
- Dropping traffic from known malicious IP addresses.
- Allowing or blocking traffic based on source or destination port.
- Implementing simple network access control lists (ACLs) for high-performance packet filtering.
Stateful Rules
Stateful rules, in contrast, consider the state of a network connection and inspect entire traffic flows. This allows for more complex inspection, such as tracking the status of a TCP connection or matching against specific session patterns. Stateful rules can be used to perform deep packet inspection, detect anomalies, and enforce more sophisticated security policies.
Use Cases for Stateful Rules:
- Intrusion detection and prevention based on traffic patterns.
- Enforcing application-layer security policies, such as blocking specific HTTP requests.
- Stateful filtering is based on a connection’s context, such as allowing established connections and dropping new connections from unknown sources.
Managed Rule Groups
Managed rule groups provide pre-configured rules maintained and updated by AWS or third-party vendors. These offer an effective way to protect your network without creating and maintaining your own rules.
They cover many use cases, such as blocking known malicious IP addresses, preventing SQL injection attacks, or enforcing content filtering policies. The official documentation provides a complete list of AWS-managed rules.
Custom Rule Groups
AWS Network Firewall allows users to create custom rule groups for more tailored security needs. These are user-defined rules that can be specifically designed to match an organisation’s unique security requirements.
Custom rule groups provide flexibility and control, allowing organisations to define rules based on their specific traffic patterns, business logic, and security policies.
Custom Rule Groups support the creation of Domain Allow/Deny Lists, domains explicitly allowed or blocked by the firewall. This feature enables organisations to control access to websites and services at the domain level, enforcing content filtering policies and preventing access to known malicious sites.
The real power, however, comes from using Suricata Rules, which are highly customisable and allow for deep packet inspection and complex traffic analysis. Suricata rules provide powerful options for creating flexible, context-aware security policies, such as detecting and blocking specific attacks or anomalies.
Suricata rules will initially invoke a steep learning curve but are well worth the investment in the long run.
Logging and Monitoring
Logging is a critical component of network security. It provides visibility into traffic patterns and potential threats and is also used for operational monitoring and troubleshooting. AWS Network Firewall generates detailed logs for each traffic flow, capturing information such as source and destination IP addresses, protocols, ports, and rule matches.
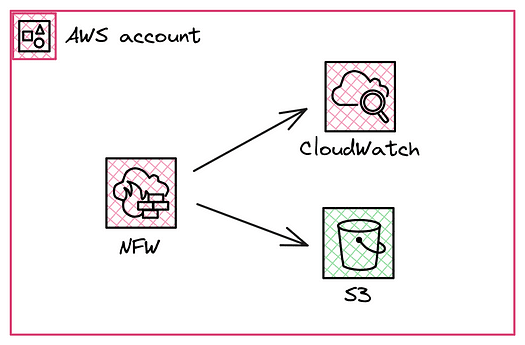
These logs can be sent to Amazon S3 or CloudWatch Logs, enabling you to store, analyse, and visualise traffic data in near real-time.
By leveraging logging, you can detect suspicious activity, troubleshoot network issues, and comply with regulatory requirements. Logs also provide valuable data for forensic investigations during a security incident.
Conclusion
AWS Network Firewall is a powerful service that enhances the security of your AWS environment. It provides a comprehensive solution for protecting resources against various threats. By leveraging managed and custom rule groups, domain white/black lists, and Suricata rules, AWS Network Firewall offers flexibility and precision in defining security policies tailored to specific organisational needs.
In the next part of the series, we will delve into the architectural patterns used to provision AWS Network firewall into single or multi-account environments and how it can be positioned to provide traffic filters for a wide range of scenarios.